Ransomware is no doubt a concern for you and your business. A cyber-attack that has hit 150 countries since its discovery on Friday afternoon, the WannaCry ransomware attack has continued to spread this weekend, impacting over 10,000 organizations and 200,000 individuals in over 150 countries. However, while measures have been taken to slow the spread of the malware, new variations have begun to surface.
Below are the threat information shared regarding recent critical vulnerabilities/threat reported.
WannaCry Ransomware That’s Hitting World Right Now Uses NSA Windows Exploit.
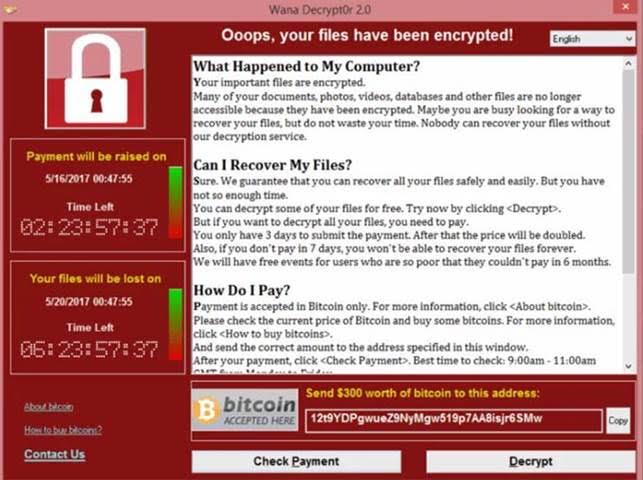
A massive ransomware campaign hit computer systems of hundreds of private companies and public organizations across the globe – which is believed to be the most massive ransomware delivery campaign to date. The Ransomware has been identified as a variant of ransomware known as WannaCry also known as ‘Wana Decrypt0r,’ ‘WannaCryptor’ or ‘WCRY’.
Most interesting about this ransomware is that WannaCry attackers are leveraging a Windows exploit harvested from the NSA called EternalBlue, which was dumped by the Shadow Brokers hacking group over a month ago. Microsoft released a patch for the vulnerability in March (MS17-010), but many users and organizations who did not patch their systems are open to attacks. The exploit has the capability to penetrate into machines running unpatched version of Windows XP through 2008 R2 by exploiting flaws in Microsoft Windows SMB Server. Once a single computer in organization is hit by the WannaCry ransomware, the worm looks for other vulnerable computers and infects them as well.
Who are affected with Ransomware Attack?
Like other nasty ransomware variants, WannaCry also blocks access to a computer or its files and demands money to unlock it. Once infected with the WannaCry ransomware, victims are asked to pay up to $300 in order to remove the infection from their PCs; otherwise, their PCs render unusable, and their files remain locked.
The ransomware targeted over 45,000 computers in 74 countries, including United States, Russia, Germany, Turkey, Italy, Philippines and Vietnam, and that the number was still growing.
How to Protect Yourself from WannaCry:
- First of all, patched your Windows machines and servers against EternalBlue exploit (MS17-010)
- You should always be suspicious of uninvited documents sent an email and should never click on links inside those documents unless verifying the source.
- Keep a good backup routine in place that makes their copies to an external storage device that is not always connected to your PC.
- Make sure that you run an active anti-virus security suite of tools on your system, and most importantly, always browse the Internet safely.
It uses strong encryption on files such as documents, images, and videos.
Sophos has issued protection for this threat:
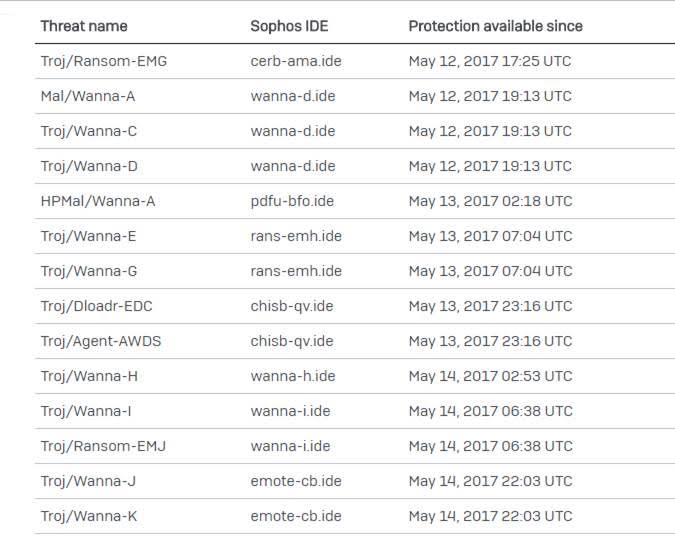
Sophos Customers using Intercept X and Sophos EXP products will also see this ransomware blocked by CryptoGuard. Please note that while Intercept X and EXP will block the underlying behavior and restore deleted or encrypted files in all cases we have seen, the offending ransomware splashscreen and note may still appear.
Sophos Intercept X is a next-generation endpoint detection and response platform focused on being thorough, efficient, and easy to use. Sophos Intercept X uses signature less exploit prevention to protect against unknown patient-zero, zero-day, and memory-resident attacks. And its advanced Crypto Guard engine stops encryption-based ransomware and rolls maliciously encrypted files back to their original states. The Root Cause Analysis tool offers a detailed but comprehensible visual map of an attack, including which files were created or altered, and offers remediation advice and tips for improving security posture in the future. Infections are neutralized with Sophos Clean technology, which thoroughly eradicates malware, including affected remnant files and registry objects – all with blazing fast scan speeds.
I’m excited to share with you that Sophos has recently released Sophos Intercept X, a new signature less anti-exploit technology, designed to stop ransomware before it takes hold.
- Sophos has released new software which stops ransomware.
- By restoring files encrypted by ransomware, we can ensure that your business is not disrupted by costly down time events.
- The good news is that this software is signature less and will not conflict with your current AV solution or any of your other security solutions. It can therefore run alongside whatever you are currently leveraging.
Anti-Exploit
- Intercept X includes technology to block all the exploits leveraged by hackers. Therefore, it will give you an advanced level of protection and block hackers from exploiting your network.
- This is a lightweight way of monitoring for and blocking advanced and zero day threats.
Root Cause Analysis
- The solution includes a Root Cause Analysis, to give you granular reporting and visual analysis to understand security incidents.
- This allows you to diagnose the source and cause of an issue, and make an accurate response. Again, this does not leverage or conflict with any third-party solutions.
You can download and start running this solution within 5 minutes. Install is easy and as the management is web based you do not have to spend time configuring your servers and broader infrastructure.
More information and trial:Sophos Intercept X

